Why is liveness detection key for biometric techniques? In this publication, we will make you familiar with some liveness detection strategies to forestall face spoofing assault or presentation attack PA. Many face spoofing attacks that come underneath the category of presentation assaults. 2D Presentation Attacks: Static 2D attacks are carried out using facial masks, photographs, or flat paper, whereas dynamic versions use multiple pictures in a sequence or display video replays. Such attacks involve utilizing 2D and 3D statistic or dynamic to deceive facial recognition software. There are quite a few methods hackers can execute face spoofing attacks. It is referred to as spoofing. Fortuitously, it’s not that widespread — most reliable websites are quick to take motion after uncovering a spoofed version.
These three modal images are segmented from the advanced background of the face space with cropping and alignment; an example of the dataset is shown in Determine 3. The dataset incorporates 21,000 video clips of 1,000 Chinese language folks. Nowadays, hackers are attempting all the things potential from 3D masks to printed pictures to bypass biometric face authentication programs. Even they’re using photographs from Fb. As an alternative to using the handcrafted labels, right here, we suggest a novel Meta-Instructor FAS MT-FAS methodology to practice a meta-instructor for supervising PA detectors extra successfully. Schedule a free identification verification demo right here lilnk. “Now, with a rapidly rising number of leads from integrators needing to integrate video analytics to their initiatives, we felt it was time to place our present companies and assist right into a formal program.” This new Channel Associate Program will provide entry to leads, quantity discounts, demo software program, advertising sources, coaching, and help.
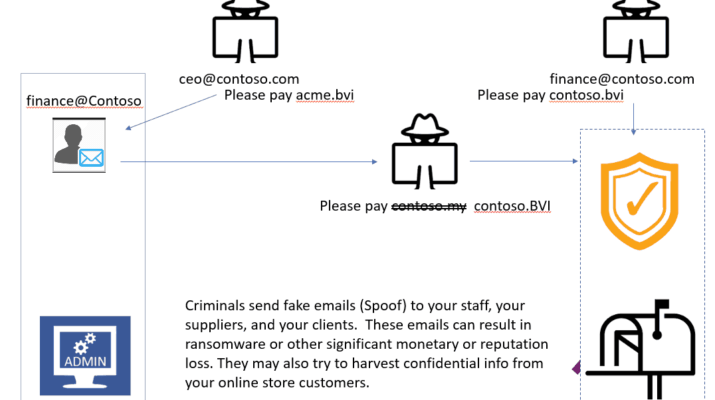
Pick one good program. For those who don’t know, facial spoofing is a course wherein a cybercriminal tries to realize illegitimate access to somebody else’s rights by utilizing a photo, video, or different materials for an authorized person’s face. Know Your Buyer KYC is a safety normal introduced by FINRA in 2009. It confirms a person as they begin an account with a shop, financial institution, or another industrial service that operates off- or online. Web of Issues or IoT is an expertise that interconnects physical objects and techniques by embedding sensors, software programs, and knowledge trade capabilities.